Tring Tring !!
Sir, I am calling on behalf of Moneywise bank.
You have been selected as the most popular customer in our group at Facebook.com
As you can see the prize is US$10000 and we would soon be transferring this amount to your account. In this regards, we would need to validate your credentials….Please provide your name as printed on the card, Date of Expiry, Card number.
Our ‘Mr Social Networker’ is on the cloud seven as he happily reads out the details.
Couple of weeks later he is dumbfounded to find all the hard earned money vanish from his account.
No, this is not a scene from any movie flick, but a dark side of the technology exploitation. Welcome to the world of Social Engineering (SE). Social Engineering is a form of hacking/cracking/fooling/spoofing people. It is also a technique that can bypass any Firewall/Antivirus/IDS etc solely because it has a dependency on exploiting the human nature. The motive is MONEY!
It can happen over phone, in person, through emails in the form of phishing, and there have been instances where freebies like CDs, USB sticks and etc loaded with malwares were given to users to be exploited later!
Unlike other forms like hacking or cracking, SE makes use of enormous amount of information that is available on internet. Bad people generally prowl around social networking sites, forums, chat rooms etc to identify probable targets and then begin their operations through sending phishing emails, putting up fake websites and inviting users, calling them, leaving tweets etc.
One of the most famous cases of SE attack involved illegal logging onto the top secret computers of US AirForce. A hacker called up the US AF facilities as Tech support pro from Sun Microsystems and they had discovered some vulnerabilities in the Solaris OS which needed to be fixed on priority, while the credentials were given to the so called engineer, within days the top secrets were out on the net!!
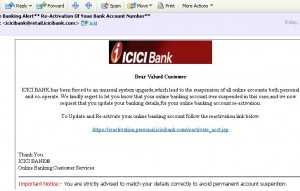
Take a look at the following email. I received it just today and it looks exactly as a genuine email from the bank on updating my account credentials:
The catch, however is the Re-activation URL pointing to some site with .bt domain and not the actual Bank’s website:
Then the URL itself is being blocked by Firefox as a reported site for Web Forgery!
So much on the internet even for not having an account with ICICI!!! Emails like above are called Phishing emails and they are one the techniques used for Social Engineering attacks.
Countermeasures:
No need to get paranoid about Social Engineering…some of the measures to counter Social Engineering is already known to you. It’s just that you are not aware of it. Take for example, would you take a chocolate or any freebie from a stranger? No right?
Similarly don’t even dare to click on links, emails etc that promise you a free Toblerone chocolate in lieu of your personal info. Spare a thought before you react to anything like a questionnaire, phone call (missed calls/wrong numbers) from unknown people, etc.
Social Networking sites like Orkut , Facebook, Myspace, Tweeter and etc are here to stay. Along with the benefits of being in touch with our friends, it also brings some privacy and security issues, however you can make your stay enjoyable by practicing vigilance, and taking due care.
Some things to consider:
• On social networking sites like Orkut, Facebook, Twitter and etc you have the options of protecting/locking your personal info (like photos, updates, birthday, tweets etc) so that it is visible to only your friends or the people you have allowed and is blocked to other users. Enable it.
• Limit the personal information there. Phone numbers, email ids, addresses etc are not worth sharing.
• Ignore unsolicited emails, calls (don’t bother to call back the missed calls).
• Read your Companies IT Security policies..Although you might find them boring, they contain valuable best practices in place across various companies and it can save your job.
• Never ever give out your personal details like Date of Birth, Name of parents, and more importantly any Banking information no matter what is offered in return. (In a survey conducted on this subject, people had given our their userid’s for some free chocolates!, )
• Some of the browsers like Firefox and Internet Explorer come with Anti-phishing filters that detect and alert you if the site you are trying to access is malicious and forged. I think they are enabled by default, if not please ensure you enable them.
• As usual, make sure your system is protected with an Antivirus (with up-to-date virus definitions), firewall and up-to-date with OS patches.
Let me know if you need any inputs.
Image Courtesy: K.U.Leuven
Further reading:
The Art of Deception by Kevin Mitnick
http://www.securityfocus.com/infocus/1533
http://www.microsoft.com/protect/computer/basics/social.mspx