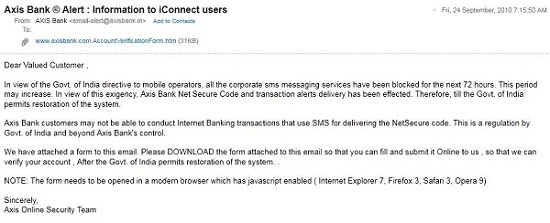
Indian politicians now take their war to the cyberspace. The ruling Indian National Congress party and the main opposition party Bharatiya Janata Party (BJP) are embroiled in a bitter war over domain redirection of BJP.COM
It all started on October 3rd a http request to http://bjp.com would redirect to Congress party’s website. It appears like some smart bloke (read Cyber Savy) at Congress or a prankster setup this redirection.
However, Congress now appears to have taken a step back with the request to http://bjp.com now landing on a parked page with ads. A Whois search for http://bjp.com owners is protected meaning the contacts have decided not disclose their details in public. The Whois records reveals that the page was further updated on October 4th (stopping the redirection to INC website) and this could be owing to the legal notice or pressure from BJP accusing congress of Cyber Theft /Cyber Fraud.
But what was Bharatiya Janata Party – BJP doing all this time? A lookup* at the history of this site reveals that it has changed ownership and content being online since 1998 for the first time. The last time this page was updated was in 2008. Since February 1998 to 2008 it was used by Brighton Journal of Philosophy (BJP) for their online journal on philosophy. So Bharatiya Janata Party did not bother to claim ownership of this domain if they considered http://BJP.COM to be their Intellectual Property, till Congress capitalized on this.
Bharatiya Janata Party might still need to watch out and take action quickly as other combinations of BJP are parked and might be available for sale. Its a hassle as even a simple typo might lead to different website and with Blackhat SEO techniques these days, it might even surpass the legitimate domain, if some one were to search for the domain.
This might serve as a reminder to many that unless you act fast and claim the ownership of your related assets online (domain names, twitter handles and other Social Networking site presence), people are just waiting to hijack them.
Cybersquatting is a common term given to such practices where a third-party buys and claims ownership of domain addresses, which would ideally belong to respective businesses, people etc and these Cybersquatters charge a fortune to give up their squatting rights if a legal course is not favorable to those who legitimately own them.
Sometime back the single bench Cyber Tribunal appellate in India asked the owners of a travel portal http://oktatabyebye.com owned by MakeMyTrip to give up their ownership of the domain and relinquish it to TATA sons because it contained the word Tata. Looks like this case may not be over as OkTataByeBye.com folks have put up their request for ‘support and help’ to retain this domain. You can read the request page HERE
* Source: Internet Archive