Twitter has to be one of the amazing innovations in recent times giving us realtime status of things happening around us. We all love to Follow and be Followed by people we know, like and relate to.
Apart from friends, relatives and colleagues who doesn’t want to follow favorite actors? sports-persons? politicians? etc and be updated on whats going on with them as well?
However, are you sure the Lewis Hamilton or Priyanka Chopra or Shashi Tharoor you are following are real and not fake? Are you following them just because your friend is following?
Here are some tips that will help you in determining if the Twitterati that you want to follow on Twitter is real or fake.
1. Is it a Verified Account
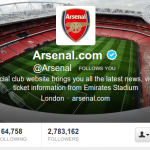
Twitter is currently beta testing ‘Verified Accounts’, wherein they confirm the identity of the person, who is tweeting using that account. As of now, it is limited to some well known personalities who have had issues with impersonation or identity confusions. A typical verified account on Twitter would look like below (Notice the blue-white check mark):
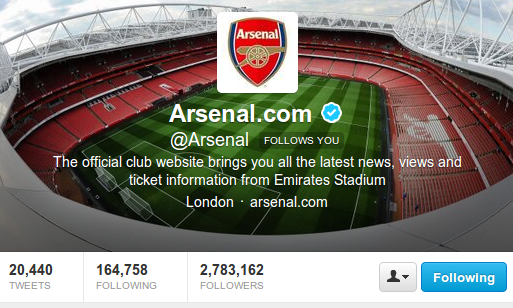
Very useful if the folk is a celebrity. Read more about Twitter Verified accounts: http://twitter.com/help/verified
2. What is the Web page of the Account holder?
Look at the Web URL posted under the twitter profile to see if it has any web page listed. A smart search on the web can reveal if it is indeed the official page or not. Again, a useful tip in case of a well known personality aka Celebrity. Some folks also point to their Facebook profiles. Again, search the web to find out if it is indeed authentic or not. Beware of any landing pages that look suspicious.
3. Look at the Tweet times.
This is interesting. All tweets have timestamp on them. Based on the time and location of the user, you can sometimes make out the fake one. Not many people would tweet in the middle of the night or early morning like 4 AM etc, atleast not on a regular basis. I had an interesting time while determining a genuineness of one such profile:
While watching the Arsenal vs Stoke match, I was a bit turned off by the horrific injury caused to Aaron Ramsey by a reckless tackle. The next morning I was looking for the info on the extent of injury and recovery time. The Gunners (Arsenal are also called as Gunners, just in case you are wondering from where did Gunners pop up) community at a social networking site had a scrap from a fan/member that Aaron Ramsey had tweeted it would take 7 months. That really ticked me off. I looked at the supposed profile of Aaron Ramsey on twitter and I had my doubts then. It was later confirmed by the timeline of tweets.
The time difference between India and UK is 5.3 hours. Twitter timeline said it was tweeted about 2 hours back. Local time (IST) when I checked was 11 AM. Which human being with a broken leg, undergoing critical treatment would think of tweeting? I think its insane. And the verified twitter account of Aaron Ramsey is here
4. Look at the Display picture
The display picture also provides a valuable information. Is it the real close up photo? or is it the twitter’s bird? For a celebrity to put a fancy or a snazzy picture of theirs from their movie posture etc is remote. Or a profile with no photo should raise the flags.
5. Look at the list of Followers and Following.
Sometimes the list of people in the Following and Followers list can provide valuable information. If its just one or two that he is following and if they too have a so similar profile, you know it is fake. Also look at who is following them…if it is a series of profiles with no photo or strange photo can be a good indicator.
NOTE: Please note that the above information is not all inclusive or foolproof. These are some basic guidelines to help you prevent follow ANY fake profiles caused due to identity theft. Please exercise caution, take due care while following ANY profile.
Appreciate your feedback. Kindly use the comments form to let me know of what you think.