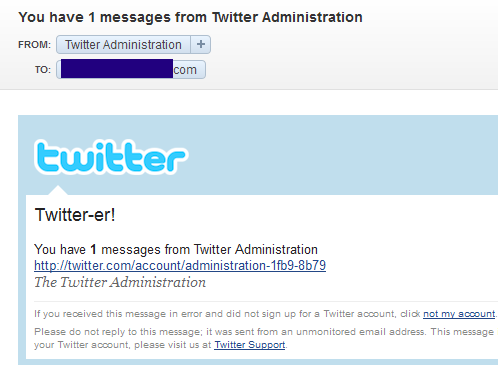
Although the concept of hacking has been used from a long time in Hollywood movies, its adoption in the Indian mainstream movies has been relatively low profile.
One of the most famous hacking scene must be Trinity (Carie Annie Moss) firing up nmap in the cult movie The Matrix Reloaded to figure out open ports on one of the power grids control machine. There have been notable other scenes and hacking concepts used in Hollywood like Wargames, Swordfish, Takedown, The Girl with the Dragon Tattoo, Independence day (probably the dumbest hacking scene in movie history – infecting alien systems with virus) and others.
As far as Indian movies go, I can remember only A Wednesday having some reasonable hacking used in our movies. Protagonist routes his call over the internet using call-bouncing to avoid detection, very plausible. The other movie I can recollect is Manirathnam’s Roja (yeah) where our hero is the cryptologist working for the Army and eventually gets kidnapped by terrorists.
Kahaani, a gripping movie about a pregnant lady searching for her lost husband in Kolkata also uses the concept of hacking to a significant extent.
Background:
During the course of the movie Vidya (whose husband is missing) & the cop figure out that Bob Biswas who is a contract killer gets the photos of his targets on his mobile phone via a website. Vidya believes if she can hack this website, she would know the IP address from where the photos are getting uploaded. Nice plot! So she hacks into the web server, and in the following screen as you can see there is the IP of the target machine!

There is no scene indicating what she does to get into the servers. To make this more authentic, probably they could have shown some web app security scanner, or even the use of eternal movie favorite nmap would have done the job of showing vulnerable services running there.
Anyways, she does get the IP by hacking into the system all the while sitting at the police station! But sadly, the command window shows (title) Traceroute! but what we see on screen is the pinging gateway.
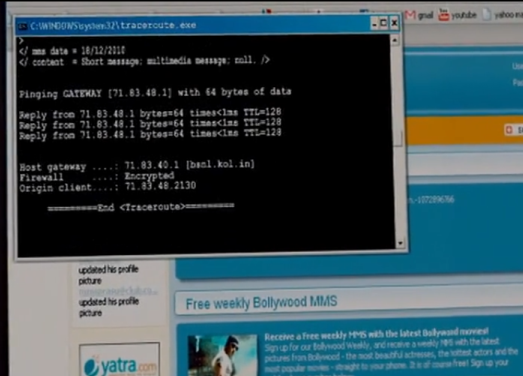
She could have used a simple whois query to find everything more about the IP address, chances are it would have given the NDC’s IP address block. For the deeper query she could have used probably used maltego or creepy…just saying. But the biggest goof up must be the stuff on the result window. Notice the last octet of the IP Address: 71.xx.xx.2130 !!!!LoL!!! Looks like someone forgot to remove the last zero or its a bad job on the photoshop because at the top of it, there is something like “Firewall:Encrypted”, which simply does not exist.
In the later part, while she physically fires up the target server it sends a message to the owner on it being Switched ON, a good lesson to be implemented in the real life too for the sensitive machines. But, most companies or data centers anyways do have notification for servers going down and coming up (restart scenario). After firing up the server she does confirm the IP addres and tries to copy the data to the USB stick.
In the real life, you wouldn’t want to do a live copy from the target machine as it may damage the integrity and hence may not be accepted in the court, if it goes through a trial. Probably the correct way of doing it is either boot the system using a live CD and then clone/image the hard-disk or files with hashes to ensure nothing was changed. Any data retrieval could be done from this cloned or copied image. These are just my thoughts…
Nevertheless with all these not-close-to-reality incidents, Kahaani is still a nice movie. To be honest, I am blown over by the acting of Vidya Balan. She looked comfortable while using the computer but am not fully convinced. There are only few movies where female actors have been shown playing with gadgets like Matrix Reloaded and the Girl with the Dragon Tattoo…Good to see such movies being made here.

NOTE: The purpose of this post is not to make fun of anyone or anything in the movie, but to highlight the points that could have given this movie an authentic touch and also make this as India’s best tech/geek/hack shown on screen! Perhaps our directors/producers should consider hiring consultants for these purposes…my consulting rates are nominal 😉 What Say Bob ?
Kahaani, now available at a discount from Flipkart.com
Related Topics: