Spotted this sometime back on one of the Axis Bank’s ATM machines in Bangalore. Any clues on what could be a demo software on a Bank’s ATM machine? It says License expired!

Related Topics:

Spotted this sometime back on one of the Axis Bank’s ATM machines in Bangalore. Any clues on what could be a demo software on a Bank’s ATM machine? It says License expired!

Related Topics:
We all know that the Indian E-commerce industry is one of the most happening sectors and there is a whole lot of competition and consolidation happening. Probably this fierce competition is also driving companies to stretch their imagination in acquiring new customers, in this case a bit too far.
The following incident happened couple of days back. I had few bonus points remaining on my credit card which I had cancelled and was looking to redeem the same. There were many options including gift vouchers at the obvious Indian E-comm portals and crossword bookstore was one of them. Although I have bought few books at crossword stores long back, I had never shopped at their online store.
And whatever memory I had about their website, I knew for sure their web address wasn’t crossword.com. So what is the next thing to do? Google it 🙂
As soon as the results loaded (as in the picture below) I was in for a surprise and a wry smile! Look at the first listing, its an ad or sponsored listing by Google. Look at it carefully, it says Crossword Bookstore but points to Flipkart.com
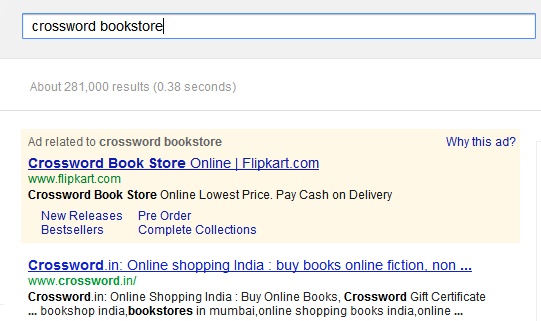
So some folks at Flipkart decided to piggyback on the “Crossword Bookstore” term and bid for this key word at Google’s Adwords. It appears that Google does not stop or forbid their customers on using competitors name in the sponsored listings for search, unless it infringes on the competitors trademark and that too for specific geolocations!For a detailed writeup on this subject, refer to Google’s Adwords policy here:
http://support.google.com/adwordspolicy/bin/answer.py?hl=en&answer=6118&topic=1346940&ctx=topic
Buying books at Crossword store was as easy and fun as it is to buy it online at Flipkart now. Did Flipkart really need to do this? I don’t think so and I feel this is a case of Blackhat SEO. So what prompted Flipkart to do this? Only they can answer but the folks at Flipkart team who bid for this keyword must have surely known what they were doing and the eventual consequences (see the update). Going by the similar instances it appears many brands do indulge in such practices and deactivate such “gray” or unethical paid listings upon notice by the victims!
At the outset it appears that Google does not have any role in it, but further researching on this topic reveals that Google has also been found liable by an Australian court for fraudulently allowing such ads. Refer the article below for details:
I had first tweeted about it here: https://twitter.com/praxprasanna/status/231324680563351552
There was no response from Flipkart, but the Crossword team on twitter were as surprised as me and I quite liked their response which had a tinge of sarcasm in it.
“@praxprasanna @Flipkart V are surprised. However v never needed to do this to get customers in our store. Happy reading.”
https://twitter.com/crossword_book/status/231639261261205506
[Update]: By the time I could finish this blog over a course of day, it appears Flipkart have stopped/deactivated their bid for the sponsored listing of the term “Crossword Bookstore” on Google Adwords. Neither have Flipkart given any clarification nor they have bothered to respond to the tweets!